使用 Docker Compose 实现镜像的推送和拉取
1. 编写 Dockerfile 及 Compose 文件
[root@elk92 dockerfile-harbor]# ll
total 20
drwxr-xr-x 2 root root 4096 Mar 25 09:29 ./
drwxr-xr-x 6 root root 4096 Mar 25 09:17 ../
-rw-r--r-- 1 root root 385 Mar 25 09:29 docker-compose.yml
-rw-r--r-- 1 root root 222 Mar 25 09:28 dockerfile
-rw-r--r-- 1 root root 232 Mar 25 09:27 Dockerfiledockerfile 文件内容
FROM alpine:3.21.3
MAINTAINER haoshuaicong
LABEL school=haoshuaicong \
class=hsc \
office=https://www.haoshuaicong.com
RUN mkdir /haoshuaicong-hsc && \
touch /haoshuaicong-hsc/haha.log
CMD ["sleep","7200"]Dockerfile 文件内容
FROM alpine:3.21.3
MAINTAINER haoshuaicong
LABEL school=haoshuaicong \
class=hsc \
office=https://www.haoshuaicong.com
RUN mkdir /haoshuaicong-hsc && \
touch /haoshuaicong-hsc/xixi.log
CMD ["tail","-f","/etc/hosts"]docker-compose.yml 文件内容
具体dockercompose 如何编写,参考docs.docker.com/reference/compose-fiel/services/
name: myapp
services:
xixi:
# 配置镜像编译
build:
# 可以理解为编译的路径"docker build -t image:tag ."
context: .
# 指定 Dockerfile 的名称
dockerfile: Dockerfile
# 编译镜像,打标签
image: 10.0.0.91/haoshuaicong-dockerfile/demo:v0.1
haha:
build:
context: .
dockerfile: dockerfile
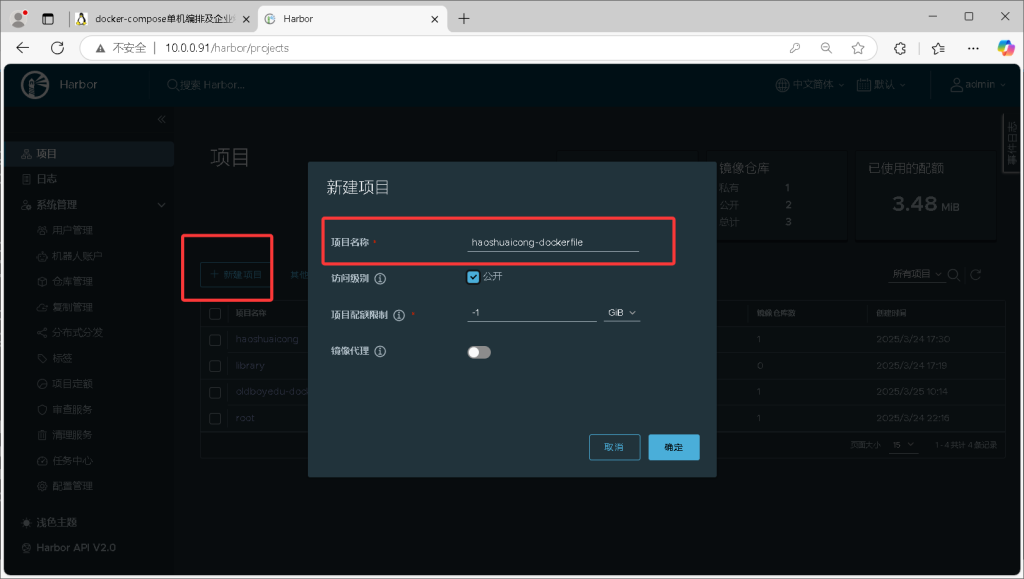
image: 10.0.0.91/haoshuaicong-dockerfile/demo:v0.2需要往91的harbor推镜像,所以需要创建一个项目目录haoshuaicong-dockerfile,来对应上面的镜像名称
2. 开始编译
会在当前路径下找dockerfile和Dockerfile文件,根据这两个文件进行编译
这样就一次编译了两个镜像,并行编译
[root@elk92 dockerfile-harbor]# docker-compose build
[+] Building 1.3s (9/9) FINISHED docker:default
=> [haha internal] load build definition from dockerfile
=> => transferring context: 2B 0.0s
=> [xixi 2/2] RUN mkdir /haoshuaicong-hsc && touch /haoshuaicong-hsc/xixi.log 1.2s
=> [xixi] exporting to image 0.1s
=> => exporting layers 0.0s
=> => writing image sha256:dff87e693fb696d71dc60b94452f9ca902b53fb092341f7e74f79112752d77ff 0.0s
=> => naming to 10.0.0.91/haoshuaicong-dockerfile/demo:v0.2 0.0s
=> => naming to 10.0.0.91/haoshuaicong-dockerfile/demo:v0.1 0.0s查看编译后的镜像:
[root@elk92 dockerfile-harbor]# docker image ls 10.0.0.91/haoshuaicong-dockerfile/demo
REPOSITORY TAG IMAGE ID CREATED SIZE
10.0.0.91/haoshuaicong-dockerfile/demo v0.2 dff87e693fb6 About a minute ago 7.83MB
10.0.0.91/haoshuaicong-dockerfile/demo v0.1 e0112d015dda About a minute ago 7.83MB3. 推送镜像到 Harbor 仓库
登录到 Harbor 仓库:
[root@elk92 dockerfile-harbor]# docker login -u admin -p 1 10.0.0.91
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded推送镜像:
[root@elk92 dockerfile-harbor]# docker-compose push
[+] Pushing 2/4
✔ Pushing haha: 2ada3d99f8ce Pushed 0.3s
⠼ Pushing xixi: 08000c18d16d Mounted from haoshuaicong-haha/redis 0.5s
# 直接push推送,会推送这两个编译好的镜像4. 访问 Harbor 的 WebUI
在浏览器中访问:http://10.0.0.91/harbor/projects/
5. 从 Harbor 仓库拉取镜像
配置 Docker 以允许访问不安全的仓库:
[root@elk91 ~]# cat /etc/docker/daemon.json
{
"insecure-registries": ["10.0.0.92:5000","10.0.0.93","10.0.0.91"]
}重启 Docker 服务:
[root@elk91 ~]# systemctl restart docker查看当前本地是否有目标镜像:
[root@elk91 ~]# docker image ls 10.0.0.91/haoshuaicong-dockerfile/demo
REPOSITORY TAG IMAGE ID CREATED SIZEdocker-compose.yaml 文件内容:
name: haoshuaicong
services:
xixi:
image: 10.0.0.91/haoshuaicong-dockerfile/demo:v0.1
haha:
image: 10.0.0.91/haoshuaicong-dockerfile/demo:v0.2拉取并启动容器:
# 你会发现,本机没有镜像,他会自动去91的harbor上拉取镜像。
[root@elk91 ~]# docker-compose up -d
[+] Running 5/5
✔ haha 1 layers [⣿] 0B/0B Pulled 0.5s
✔ 3bbb9eaecec8 Pull complete
[+] Running 3/3
✔ Network haoshuaicong_default Created 0.1s
✔ Container haoshuaicong-xixi-1 Started 0.1s 查看容器状态:
[root@elk91 ~]# docker-compose ps
NAME IMAGE COMMAND SERVICE CREATED STATUS PORTS
haoshuaicong-haha-1 10.0.0.91/haoshuaicong-dockerfile/demo:v0.2 "sleep 7200" haha 51 seconds ago Up 50 seconds
haoshuaicong-xixi-1 10.0.0.91/haoshuaicong-dockerfile/demo:v0.1 "tail -f /etc/hosts" xixi 51 seconds ago Up 50 seconds 再次查看本地镜像:
[root@elk91 ~]# docker image ls 10.0.0.91/haoshuaicong-dockerfile/demo
REPOSITORY TAG IMAGE ID CREATED SIZE
10.0.0.91/haoshuaicong-dockerfile/demo v0.1 e0112d015dda 9 minutes ago 7.83MB
10.0.0.91/haoshuaicong-dockerfile/demo v0.2 dff87e693fb6 9 minutes ago 7.83MB彩蛋:解决 Harbor 无法访问的问题
1. 进入到 Harbor 的安装目录
[root@elk91 ~]# cd /usr/local/harbor/
[root@elk91 harbor]# ll
total 636536
drwxr-xr-x 3 root root 4096 Mar 24 18:06 ./
drwxr-xr-x 18 root root 4096 Mar 24 18:03 ../
drwxr-xr-x 3 root root 4096 Mar 24 18:05 common/
-rw-r--r-- 1 root root 3646 Jan 16 22:10 common.sh
-rw-r--r-- 1 root root 5828 Mar 24 18:06 docker-compose.yml
-rw-r--r-- 1 root root 651727378 Jan 16 22:11 harbor.v2.12.2.tar.gz
-rw-r--r-- 1 root root 14345 Mar 24 18:04 harbor.yml
-rw-r--r-- 1 root root 14288 Jan 16 22:10 harbor.yml.tmpl
-rwxr-xr-x 1 root root 1976 Mar 24 18:06 install.sh*
-rw-r--r-- 1 root root 11347 Jan 16 22:10 LICENSE
-rwxr-xr-x 1 root root 2211 Jan 16 22:10 prepare*2. 停止服务
[root@elk91 harbor]# docker-compose down -t 0
[+] Running 10/10
✔ Container nginx Removed 0.0s
✔ Container harbor-jobservice Removed 0.0s
✔ Container registryctl Removed 0.2s
✔ Network harbor_harbor Removed 0.2s 3. 启动服务
[root@elk91 harbor]# docker-compose up -d
[+] Building 0.0s (0/0) docker:default
[+] Running 10/10
✔ Network harbor_harbor Created 0.1s
✔ Container harbor-log Started
✔ Container harbor-core Started 0.0s
✔ Container nginx Started 0.1s
✔ Container harbor-jobservice Started 0.1s 4. 查看容器的运行列表
[root@elk91 harbor]# docker-compose ps -a
NAME IMAGE COMMAND SERVICE CREATED STATUS PORTS
harbor-core goharbor/harbor-core:v2.12.2 "/harbor/entrypoint.…" core 43 seconds ago Up 41 seconds (healthy)
harbor-db goharbor/harbor-db:v2.12.2 "/docker-entrypoint.…" postgresql 43 seconds ago Up 42 seconds (healthy)
harbor-jobservice goharbor/harbor-jobservice:v2.12.2 "/harbor/entrypoint.…" jobservice 43 seconds ago Up 40 seconds (healthy)
harbor-log goharbor/harbor-log:v2.12.2 "/bin/sh -c /usr/loc…" log 43 seconds ago Up 42 seconds (healthy) 127.0.0.1:1514->10514/tcp
harbor-portal goharbor/harbor-portal:v2.12.2 "nginx -g 'daemon of…" portal 43 seconds ago Up 41 seconds (healthy)
nginx goharbor/nginx-photon:v2.12.2 "nginx -g 'daemon of…" proxy 43 seconds ago Up 39 seconds (healthy) 0.0.0.0:80->8080/tcp, :::80->8080/tcp
redis goharbor/redis-photon:v2.12.2 "redis-server /etc/r…" redis 43 seconds ago Up 41 seconds (healthy)
registry goharbor/registry-photon:v2.12.2 "/home/harbor/entryp…" registry 43 seconds ago Up 41 seconds (healthy)
registryctl goharbor/harbor-registryctl:v2.12.2 "/home/harbor/start.…" registryctl 43 seconds ago Up 41 seconds (healthy) Harbor 仓库的用户管理
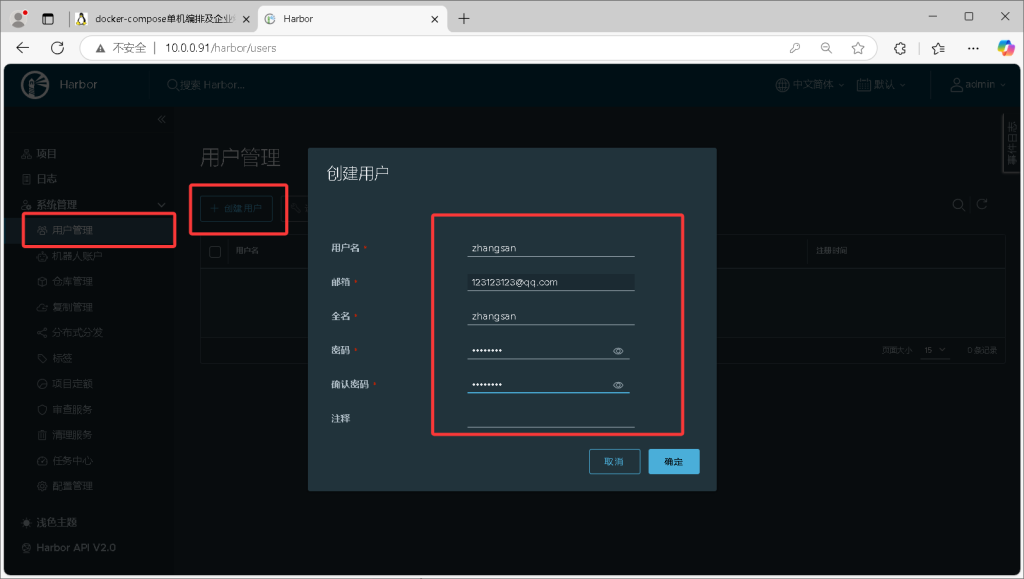
私有项目,不登录无法拉取,这里指定一个用户,让他有对应项目的拉取权限
1. 创建用户
2. 将私有项目绑定到某个到 zhangsan 用户
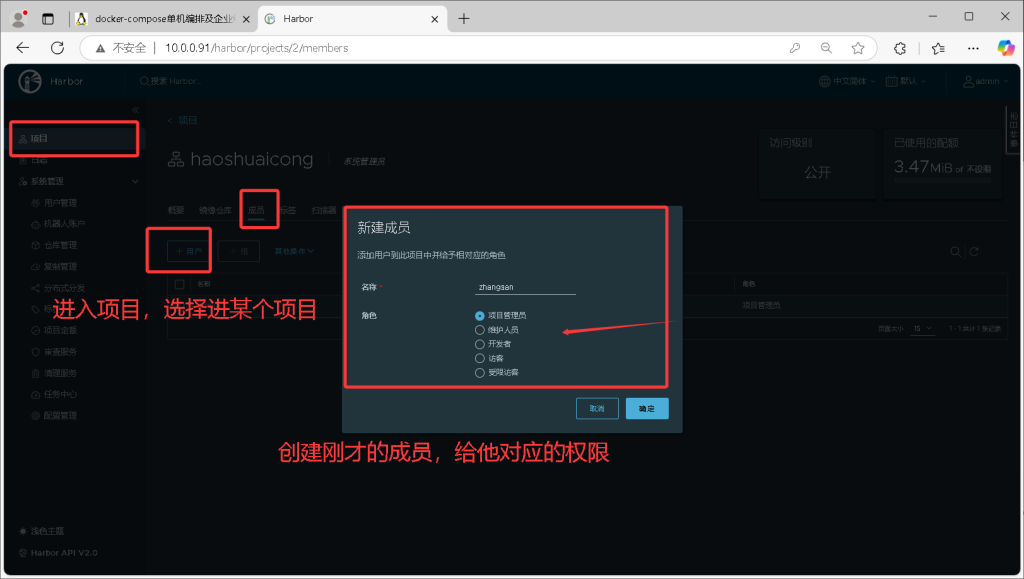
3. 测试验证
本案例将 zhangsan 用户和 haoshuaicong 项目绑定,不登录相应权限账号 haoshuaicong – xixi 私有项目是无法拉取。
尝试未登录状态下拉取 haoshuaicong-haha 项目的镜像:
[root@elk91 ~]# docker pull 10.0.0.91/haoshuaicong-haha/hello-world:latest
Error response from daemon: unauthorized: unauthorized to access repository: haoshuaicong-haha/hello-world, action: pull: unauthorized to access repository: haoshuaicong-haha/hello-world, action: pull使用 zhangsan 用户登录 Harbor 仓库:
[root@elk91 ~]# docker login -u zhangsan -p abc123123 10.0.0.91
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded查看登录后的认证信息:
[root@elk91 ~]# cat /root/.docker/config.json
{
"auths": {
"10.0.0.91": {
"auth": "bGludXg5NjpMaW51eDk2QDIwMjU="
}
}
}解码认证信息:
[root@elk91 ~]# echo bGludXg5NjpMaW51eDk2QDIwMjU=| base64 -d;echo
hsc:hsc@2025登录后拉取 haoshuaicong-haha 项目的镜像:
[root@elk91 ~]# docker pull 10.0.0.91/haoshuaicong-haha/hello-world:latest
latest: Pulling from haoshuaicong/hello-world
e6590344b1a5: Pull complete
Digest: sha256:7565f2c7034d87673c5ddc3b1b8e97f8da794c31d9aa73ed26afffa1c8194889
Status: Downloaded newer image for 10.0.0.91/haoshuaicong-haha/hello-world:latest
10.0.0.91/haoshuaicong-haha/hello-world:latest查看拉取的镜像:
[root@elk91 ~]# docker image ls 10.0.0.91/haoshuaicong-haha/hello-world:latest
REPOSITORY TAG IMAGE ID CREATED SIZE
10.0.0.91/haoshuaicong-haha/hello-world latest 74cc54e27dc4 2 months ago 10.1kB尝试拉取 haoshuaicong-xixi 项目的镜像(由于用户未绑定该项目,拉取失败):
[root@elk91 ~]# docker pull 10.0.0.91/haoshuaicong-xixi/alpine:3.21.3
Error response from daemon: unauthorized: unauthorized to access repository: haoshuaicong-xixi/alpine, action: pull: unauthorized to access repository: haoshuaicong-xixi/alpine, action: pullHarbor 的 HTTPS 配置
1. 环境准备
- 域名与 IP 映射:
harbor250.haoshuaicong.com对应10.0.0.250 - 硬件配置:1C,2G+ 内存,50GB+ 存储
2. 准备 Harbor 安装包
[root@elk93 ~]# scp harbor-offline-installer-v2.12.2.tgz haoshuaicong-autoinstall-docker-docker-compose.tar.gz 10.0.0.250:~3. 安装 Docker、Docker Compose 并解压 Harbor 安装包
3.1 安装 Docker 和 Docker Compose
[root@harbor250.haoshuaicong.com ~]# tar xf haoshuaicong-autoinstall-docker-docker-compose.tar.gz
[root@harbor250.haoshuaicong.com ~]# ./install-docker.sh i3.2 解压 Harbor 安装包
[root@harbor250.haoshuaicong.com ~]# tar xf harbor-offline-installer-v2.12.2.tgz -C /usr/local/4. 配置 CA 证书
4.1 进入到 Harbor 程序的根目录
[root@harbor250.haoshuaicong.com ~]# cd /usr/local/harbor/
[root@harbor250.haoshuaicong.com harbor]# ll
total 636508
drwxr-xr-x 2 root root 4096 Mar 25 10:30 ./
drwxr-xr-x 11 root root 4096 Mar 25 10:30 ../
-rw-r--r-- 1 root root 3646 Jan 16 22:10 common.sh
-rw-r--r-- 1 root root 651727378 Jan 16 22:11 harbor.v2.12.2.tar.gz
-rw-r--r-- 1 root root 14288 Jan 16 22:10 harbor.yml.tmpl
-rwxr-xr-x 1 root root 1975 Jan 16 22:10 install.sh*
-rw-r--r-- 1 root root 11347 Jan 16 22:10 LICENSE
-rwxr-xr-x 1 root root 2211 Jan 16 22:10 prepare*4.2 创建证书存放目录
[root@harbor250.haoshuaicong.com harbor]# mkdir -pv certs/{ca,harbor-server,docker-client}
mkdir: created directory 'certs'
mkdir: created directory 'certs/ca'
mkdir: created directory 'certs/harbor-server'
mkdir: created directory 'certs/docker-client'
[root@harbor250.haoshuaicong.com harbor]# tree certs
certs
├── ca
├── docker-client
└── harbor-server
3 directories, 0 files4.3 创建 CA 的私钥
ca证书的私钥
[root@harbor250.haoshuaicong.com harbor]# cd certs/
[root@harbor250.haoshuaicong.com certs]# openssl genrsa -out ca/ca.key 4096
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ └── ca.key
├── docker-client
└── harbor-server
3 directories, 1 file4.4 基于自建的 CA 私钥创建 CA 证书(注意,证书签发的域名范围)
签发证书,只要是xxx.haoshuaicong.com的域名范围都行,子域名都可。CN=haoshuaicong.com
[root@harbor250.haoshuaicong.com certs]# openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=haoshuaicong.com" \
-key ca/ca.key \
-out ca/ca.crt
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── docker-client
└── harbor-server
3 directories, 2 files4.5 查看自建证书信息
查看证书信息
[root@harbor250.haoshuaicong.com certs]# openssl x509 -in ca/ca.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
3d:fb:57:45:7c:cc:15:d5:ce:04:a2:1d:80:0a:18:49:88:8d:cd:9a
Signature Algorithm: sha512WithRSAEncryption
Issuer: C = CN, ST = Beijing, L = Beijing, O = example, OU = Personal, CN = haoshuaicong.com
Validity
Not Before: Mar 25 02:33:25 2025 GMT
Not After : Mar 23 02:33:25 2035 GMT
Subject: C = CN, ST = Beijing, L = Beijing, O = example, OU = Personal, CN = haoshuaicong.com
...5. 配置 Harbor 服务端证书
5.1 生成 Harbor 服务器的私钥
这里子域名是harbor250.xxxx 也符合上面证书的范围要求
[root@harbor250.haoshuaicong.com certs]# openssl genrsa -out harbor-server/harbor250.haoshuaicong.com.key 4096
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── docker-client
└── harbor-server
└── harbor250.haoshuaicong.com.key
3 directories, 3 files5.2 Harbor 服务器基于私钥签发证书认证请求(CSR 文件),让自建 CA 认证
基于私钥签发对应的csr证书认证请求(CSR 文件)
[root@harbor250.haoshuaicong.com certs]# openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=harbor250.haoshuaicong.com" \
-key harbor-server/harbor250.haoshuaicong.com.key \
-out harbor-server/harbor250.haoshuaicong.com.csr
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── docker-client
└── harbor-server
├── harbor250.haoshuaicong.com.csr
└── harbor250.haoshuaicong.com.key
3 directories, 4 files5.3 生成 x509 v3 的扩展文件用于认证
[root@harbor250.haoshuaicong.com certs]# cat > harbor-server/v3.ext <<-EOF
[root@harbor250.haoshuaicong.com certs]# cat > harbor-server/v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=harbor250.haoshuaicong.com
EOF
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── docker-client
└── harbor-server
├── harbor250.haoshuaicong.com.csr
├── harbor250.haoshuaicong.com.key
└── v3.ext
3 directories, 5 files5.4 基于 x509 v3 的扩展文件认证签发 Harbor server 证书
基于v3.ext、ca.key、csr 生成 crt 证书,out表示生成输出
[root@harbor250.haoshuaicong.com certs]# openssl x509 -req -sha512 -days 3650 \
-extfile harbor-server/v3.ext \
-CA ca/ca.crt -CAkey ca/ca.key -CAcreateserial \
-in harbor-server/harbor250.haoshuaicong.com.csr \
-out harbor-server/harbor250.haoshuaicong.com.crt
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── docker-client
└── harbor-server
├── harbor250.haoshuaicong.com.crt
├── harbor250.haoshuaicong.com.csr
├── harbor250.haoshuaicong.com.key
└── v3.ext
3 directories, 6 files5.5 修改 Harbor 的配置文件使用自建证书
更改hostname 和证书目录即可,hostname是你对应的域名
[root@harbor250.haoshuaicong.com certs]# cp ../harbor.yml{.tmpl,}
[root@harbor250.haoshuaicong.com certs]# vim ../harbor.yml
...
hostname: harbor250.haoshuaicong.com
https:
...
certificate: /usr/local/harbor/certs/harbor-server/harbor250.haoshuaicong.com.crt
private_key: /usr/local/harbor/certs/harbor-server/harbor250.haoshuaicong.com.key
...
harbor_admin_password: 1
...
data_volume: /var/lib/harbor
... 5.6 安装 Harbor 服务
[root@harbor250.haoshuaicong.com certs]# ../install.sh
[Step 0]: checking if docker is installed ...
[Step 2]: loading Harbor images ...
...
[Step 5]: starting Harbor ...
[+] Building 0.0s (0/0) docker:default
[+] Running 10/10
✔ Network harbor_harbor Created 0.0s
✔ Container harbor-jobservice Started 0.0s
✔ ----Harbor has been installed and started successfully.----6. 访问 Harbor 的 WebUI
6.1 在 Windows 添加 hosts 文件解析如下
10.0.0.250 harbor250.haoshuaicong.com6.2 访问测试
https://harbor250.haoshuaicong.com/harbor/projects/1/repositories到这里,你的服务端已经准备好了
客户端常见的报错
Q1: dial tcp: lookup harbor250.haoshuaicong.com on 127.0.0.53:53: no such host
[root@elk93 ~]# docker login -u admin -p 1 harbor250.haoshuaicong.com
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Error response from daemon: Get "https://harbor250.haoshuaicong.com/v2/": dial tcp: lookup harbor250.haoshuaicong.com on 127.0.0.53:53: no such host- 问题原因:无法解析域名主机。127.0.0.53:53 表示DNS解析问题
- 解决方案:配置 hosts 解析即可。
Q2: x509: certificate signed by unknown authority
[root@elk93 ~]# docker login -u admin -p 1 harbor250.haoshuaicong.com
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Error response from daemon: Get "https://harbor250.haoshuaicong.com/v2/": x509: certificate signed by unknown authority- 问题原因:证书不安全,可能是服务端自建证书。
- 解决方案:添加证书信任,参考下面的。
参考链接
- https://goharbor.io/docs/1.10/install-config/configure-https/#generate-a-certificate-authority-certificate
- https://www.cnblogs.com/haoshuaicong/p/17153673.html
配置 Docker 客户端证书实战案例
1. 生成 Docker 客户端证书
把这几个证书文件,放到客户端目录。需要的时候拷贝到客户端即可,添加证书信任。
注意,第二个要crt改名为cert
[root@harbor250.haoshuaicong.com certs]# cp ca/ca.crt harbor-server/harbor250.haoshuaicong.com.key docker-client/
[root@harbor250.haoshuaicong.com certs]# cp harbor-server/harbor250.haoshuaicong.com.crt docker-client/harbor250.haoshuaicong.com.cert
[root@harbor250.haoshuaicong.com certs]# tree
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── docker-client
│ ├── ca.crt
│ ├── harbor250.haoshuaicong.com.cert
│ └── harbor250.haoshuaicong.com.key
└── harbor-server
├── harbor250.haoshuaicong.com.crt
├── harbor250.haoshuaicong.com.csr
├── harbor250.haoshuaicong.com.key
└── v3.ext
3 directories, 9 files2. Docker 客户端创建自建证书的目录结构(注意域名的名称和目录要一致)
[root@elk91 ~]# mkdir -pv /etc/docker/certs.d/harbor250.haoshuaicong.com/
mkdir: created directory '/etc/docker/certs.d'
mkdir: created directory '/etc/docker/certs.d/harbor250.haoshuaicong.com/'3. 拷贝 Docker client 证书文件到客户端
[root@elk91 ~]# ll /etc/docker/certs.d/harbor250.haoshuaicong.com/
total 8
drwxr-xr-x 2 root root 4096 Mar 25 11:00 ./
drwxr-xr-x 3 root root 4096 Mar 25 11:00 ../
[root@elk91 ~]# scp harbor250.haoshuaicong.com:/usr/local/harbor/certs/docker-client/* /etc/docker/certs.d/harbor250.haoshuaicong.com/
...
root@harbor250.haoshuaicong.com's password:
ca.crt 100% 2049 4.3MB/s 00:00
harbor250.haoshuaicong.com.cert 100% 2155 1.6MB/s 00:00
harbor250.haoshuaicong.com.key 100% 3268 7.6MB/s 00:00
[root@elk91 ~]# ll /etc/docker/certs.d/harbor250.haoshuaicong.com/
total 20
drwxr-xr-x 2 root root 4096 Mar 25 11:01 ./
drwxr-xr-x 3 root root 4096 Mar 25 11:00 ../
-rw-r--r-- 1 root root 2049 Mar 25 11:01 ca.crt
-rw-r--r-- 1 root root 2155 Mar 25 11:01 harbor250.haoshuaicong.com.cert
-rw------- 1 root root 3268 Mar 25 11:01 harbor250.haoshuaicong.com.key4. 客户端登录测试
[root@elk91 ~]# docker login -u admin -p 1 harbor250.haoshuaicong.com
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[root@elk91 ~]# cat /root/.docker/config.json
{
"auths": {
"10.0.0.91": {
"auth": "bGludXg5NjpMaW51eDk2QDIwMjU="
},
"harbor250.haoshuaicong.com": {
"auth": "YWRtaW46MQ=="
}
}
}[root@elk91 ~]#
[root@elk91 ~]# echo YWRtaW46MQ== | base64 -d;echo
admin:15. 推送镜像
[root@elk91 ~]# docker tag 10.0.0.91/haoshuaicong-haha/hello-world:latest harbor250.haoshuaicong.com/library/hello-world
[root@elk91 ~]# docker push harbor250.haoshuaicong.com/library/hello-world
Using default tag: latest
The push refers to repository [harbor250.haoshuaicong.com/library/hello-world]
63a41026379f: Pushed
latest: digest: sha256:7565f2c7034d87673c5ddc3b1b8e97f8da794c31d9aa73ed26afffa1c8194889 size: 5246. 拉取镜像
[root@elk93 ~]# scp -r 10.0.0.91:/etc/docker/certs.d/ /etc/docker
root@10.0.0.91's password:
harbor250.haoshuaicong.com.cert 100% 2155 6.0MB/s 00:00
ca.crt 100% 2049 1.7MB/s 00:00
harbor250.haoshuaicong.com.key 100% 3268 3.9MB/s 00:00
[root@elk93 ~]# docker pull harbor250.haoshuaicong.com/library/hello-world
Using default tag: latest
latest: Pulling from library/hello-world
e6590344b1a5: Pull complete
Digest: sha256:7565f2c7034d87673c5ddc3b1b8e97f8da794c31d9aa73ed26afffa1c8194889
Status: Downloaded newer image for harbor250.haoshuaicong.com/library/hello-world:latest
harbor250.haoshuaicong.com/library/hello-world:latest
[root@elk93 ~]# docker image ls harbor250.haoshuaicong.com/library/hello-world
REPOSITORY TAG IMAGE ID CREATED SIZE
harbor250.haoshuaicong.com/library/hello-world latest 74cc54e27dc4 2 months ago 10.1kB权威机构颁发的证书 HTTPS 配置实战
1. 下载证书
[root@elk93 ~]# wget http://192.168.16.253/hsc/Docker/day12-/notes/harbor.haoshuaicong.com_nginx.zip2. 解压证书
[root@elk93 ~]# unzip harbor.haoshuaicong.com_nginx.zip -d /usr/local/harbor/3. 修改 Harbor 的配置文件
[root@elk93 ~]# cd /usr/local/harbor/
[root@elk93 harbor]# vim harbor.yml在 harbor.yml 文件中做如下修改:
...
hostname: harbor.haoshuaicong.com
...
https:
...
certificate: /usr/local/harbor/harbor.haoshuaicong.com_nginx/harbor.haoshuaicong.com_bundle.crt
private_key: /usr/local/harbor/harbor.haoshuaicong.com_nginx/harbor.haoshuaicong.com.key4. 重新安装
[root@elk93 harbor]# ./prepare[root@elk93 harbor]# ./install.sh安装结果示例:
...
[Step 5]: starting Harbor ...
[+] Building 0.0s (0/0) docker:default
[+] Running 10/10
✔ Network harbor_harbor Created 0.1s
✔ Container harbor-log Started 0.0s
✔ Container nginx Started 0.0s
✔ Container harbor-jobservice Started 0.0s
✔ ----Harbor has been installed and started successfully.----
[root@elk93 harbor]# 5. Windows 访问测试
5.1 Windows 添加解析
在 Windows 的 hosts 文件(通常位于 C:\Windows\System32\drivers\etc\hosts)中添加以下内容:
10.0.0.93 harbor.haoshuaicong.com5.2 访问测试
在浏览器中访问 https://harbor.haoshuaicong.com/harbor/projects
6. Docker 客户端测试
6.1 添加 hosts 解析
[root@elk91 ~]# echo 10.0.0.93 harbor.haoshuaicong.com >> /etc/hosts6.2 登录测试
[root@elk91 ~]# docker login -u admin -p 1 harbor.haoshuaicong.com可能出现的提示信息:
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[root@elk91 ~]# Docker Hub 官方镜像推送和拉取示例
1. 注册 Docker Hub 账号
前往 https://hub.docker.com/ 注册 Docker Hub 账号。
2. 登录 Docker Hub
用户名密码是你docker官方账号和密码,你注册的docker账号
[root@elk92 dockerfile - harbor]# docker login -u 用户名
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials - store
Login Succeeded查看登录配置信息:
[root@elk92 dockerfile - harbor]# cat /root/.docker/config.json
{
"auths": {
"10.0.0.91": {
"auth": "YWRtaW46MQ=="
},
"10.0.0.93": {
"auth": "YWRtaW46MQ=="
},
"https://index.docker.io/v1/": {
"auth": "aW5wb3JsOmNhbzE5MzAxOS4="
}
}
}解码认证信息:
[root@elk92 dockerfile - harbor]# echo aW5wb3JsOmNhbzE5MzAxOS4= | base64 -d
inporl:cao193019.3. 在 Docker Hub 的 Web UI 创建仓库
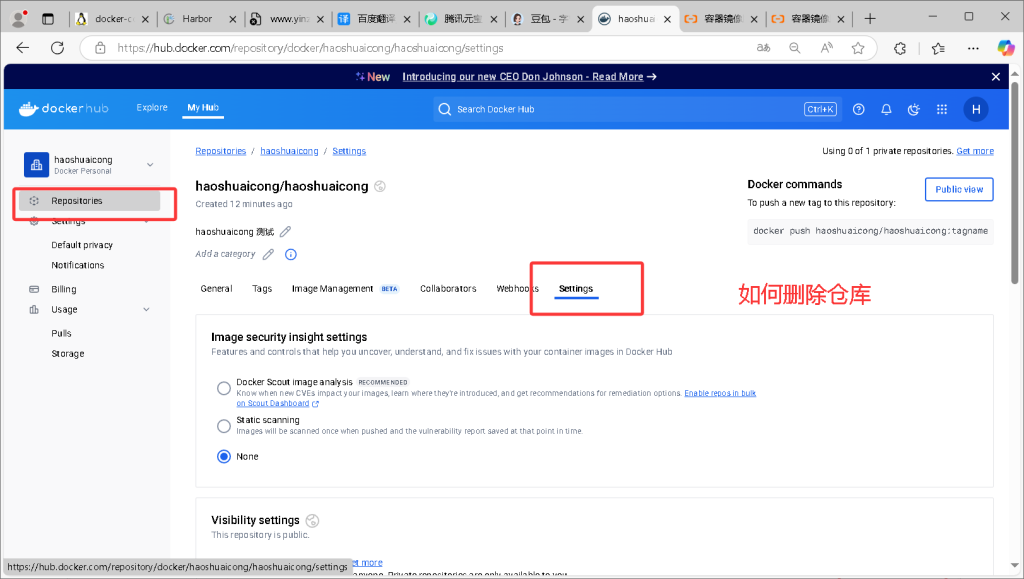
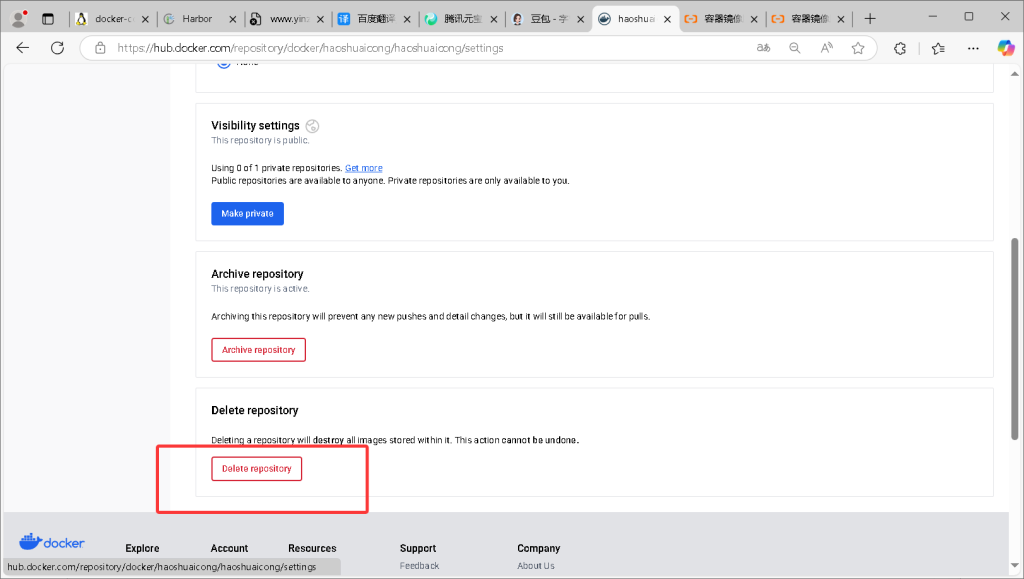
在 Docker Hub 的 Web UI 界面创建名为 haoshuaicong 的仓库。
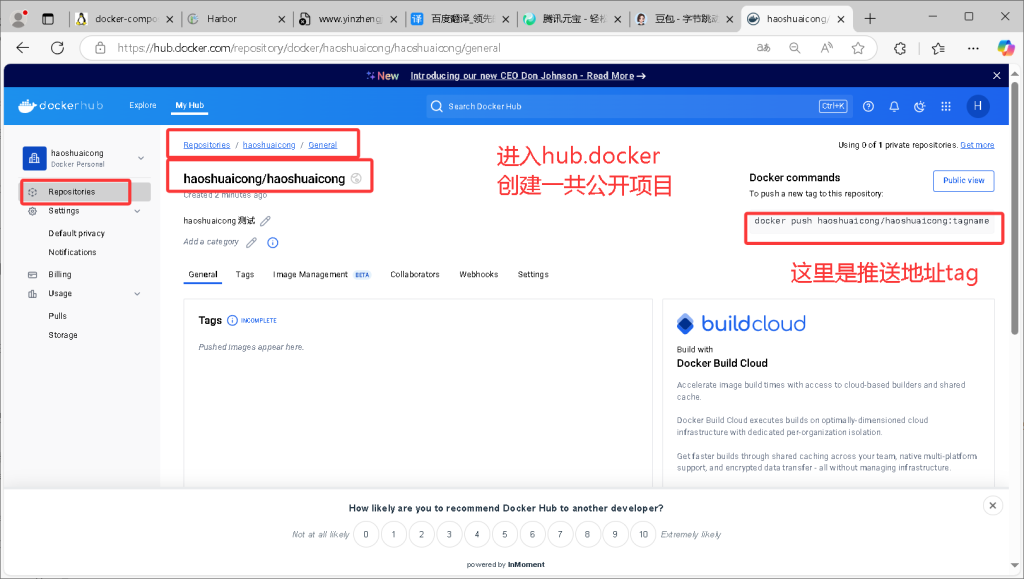
4. 将本地镜像推送到 Docker Hub
[root@elk92 dockerfile - harbor]# docker tag busybox:1.36.1 inporl/haoshuaicong - hsc:busybox
[root@elk92 dockerfile - harbor]# docker push inporl/haoshuaicong - hsc:busybox
The push refers to repository [docker.io/inporl/haoshuaicong - hsc]
d41208ff92a2: Mounted from library/busybox
busybox: digest: sha256:ee1dce1e7be987d23d9f60a84f8e47a4e76469e935c150bb112472247dc9b67c size: 5275. 在 Web UI 访问测试
具体操作见相关视频。
6. 从 Docker Hub 拉取镜像
[root@elk92 ~]# docker image rm inporl/haoshuaicong - hsc:busybox
Untagged: inporl/haoshuaicong - hsc:busybox
Untagged: inporl/haoshuaicong - hsc@sha256:ee1dce1e7be987d23d9f60a84f8e47a4e76469e935c150bb112472247dc9b67c
[root@elk92 ~]# docker image ls inporl/haoshuaicong - hsc:busybox
REPOSITORY TAG IMAGE ID CREATED SIZE
[root@elk92 ~]# docker pull inporl/haoshuaicong - hsc:busybox
busybox: Pulling from inporl/haoshuaicong - hsc
Digest: sha256:ee1dce1e7be987d23d9f60a84f8e47a4e76469e935c150bb112472247dc9b67c
Status: Downloaded newer image for inporl/haoshuaicong - hsc:busybox
docker.io/inporl/haoshuaicong - hsc:busybox
[root@elk92 ~]# docker image ls inporl/haoshuaicong - hsc:busybox
REPOSITORY TAG IMAGE ID CREATED SIZE
inporl/haoshuaicong - hsc busybox 2d61ae04c2b8 22 months ago 4.27MB7. 退出登录
[root@elk92 ~]# cat /root/.docker/config.json
{
"auths": {
"10.0.0.91": {
"auth": "YWRtaW46MQ=="
},
"10.0.0.93": {
"auth": "YWRtaW46MQ=="
},
"https://index.docker.io/v1/": {
"auth": "aW5wb3JsOmNhbzE5MzAxOS4="
}
}
}
[root@elk92 ~]# docker logout
Removing login credentials for https://index.docker.io/v1/
[root@elk92 ~]# cat /root/.docker/config.json
{
"auths": {
"10.0.0.91": {
"auth": "YWRtaW46MQ=="
},
"10.0.0.93": {
"auth": "YWRtaW46MQ=="
}
}
}阿里云第三方镜像仓库管理实战
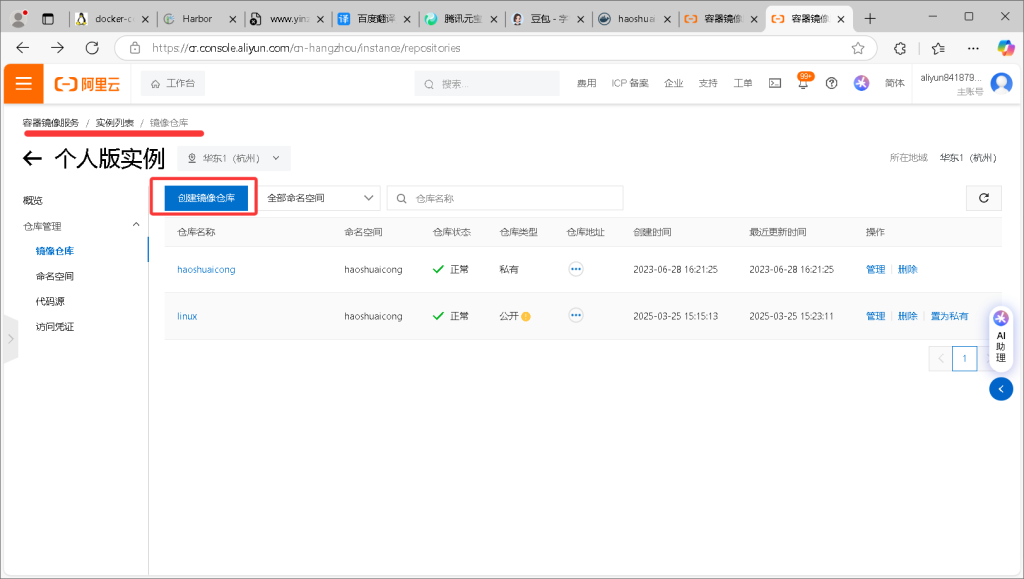
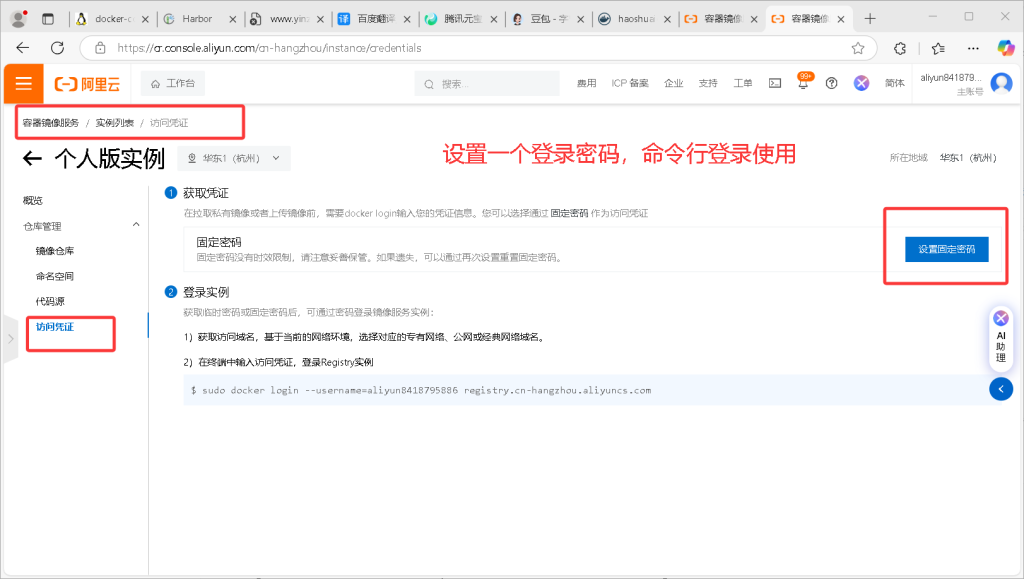
1. 新建仓库
2. 命令行登录阿里云账号
[root@elk91 ~]# docker login -u haoshuaicong registry.cn - hangzhou.aliyuncs.com
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials - store
Login Succeeded3. 推送镜像到阿里云
[root@elk91 ~]# docker tag harbor250.haoshuaicong.com/library/hello - world:latest registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc:v1
[root@elk91 ~]# docker push registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc:v1
The push refers to repository [registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc]
63a41026379f: Pushed
v1: digest: sha256:7565f2c7034d87673c5ddc3b1b8e97f8da794c31d9aa73ed26afffa1c8194889 size: 5244. 从阿里云拉取镜像
[root@elk93 ~]# docker pull registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc:v1
v1: Pulling from haoshuaicong - test/hsc
Digest: sha256:7565f2c7034d87673c5ddc3b1b8e97f8da794c31d9aa73ed26afffa1c8194889
Status: Downloaded newer image for registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc:v1
registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc:v1
[root@elk93 ~]# docker image ls registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc:v1
REPOSITORY TAG IMAGE ID CREATED SIZE
registry.cn - hangzhou.aliyuncs.com/haoshuaicong - test/hsc v1 74cc54e27dc4 2 months ago 10.1kB5. 删除阿里云镜像
略
6. 客户端退出登录
[root@elk91 ~]# docker logout registry.cn - hangzhou.aliyuncs.com
Removing login credentials for registry.cn - hangzhou.aliyuncs.com
[root@elk91 ~]# containerd 容器管理工具快速入门 * * * * *🍄💋
1. 什么是 Containerd
Containerd 是一款轻量级容器管理工具,支持对镜像、容器、存储卷等进行管理。
相较于 Docker,它更为轻量级,不过其功能上不支持网络,需要单独部署 CNI (网络)组件。
另外,与 Docker 不同,ctr 支持名称空间,可将镜像、容器、任务划分到不同的名称空间,实现一定程度的资源隔离。
而 Docker 底层调用了 Containerd 来管理容器和镜像,同时对使用方式进行了优化,还支持网络、DNS 解析等功能。
2. ctr 管理名称空间
2.1 添加套接字映射
如果链接了这个,导致docker无法启动报错,可以apt安装conainerd解决。
# 直接用的话,报错找不到sock套接字。我们把我们的sock指定到他要的路径即可
[root@elk92 image]# ctr ns ls
ctr: failed to dial "/run/containerd/containerd.sock": context deadline exceeded: connection error: desc = "transport: error while dialing: dial unix:///run/containerd/containerd.sock: timeout"
[root@elk92 image]#
[root@elk91 ~]# ln -svf /var/run/docker/containerd/containerd.sock /run/containerd/
'/run/containerd/containerd.sock' -> '/var/run/docker/containerd/containerd.sock'
[root@elk91 ~]#
[root@elk91 ~]# ctr ns ls # 查看名称空间
NAME LABELS
moby
[root@elk91 ~]# 2.2 创建常见名称空间
[root@elk91 ~]# ctr ns create haoshuaicong
[root@elk91 ~]#
[root@elk91 ~]# ctr ns ls
NAME LABELS
moby
haoshuaicong
[root@elk91 ~]# 2.3 删除名称空间
[root@elk91 ~]# ctr ns create hsc
[root@elk91 ~]#
[root@elk91 ~]# ctr ns ls
NAME LABELS
hsc
moby
haoshuaicong
[root@elk91 ~]#
[root@elk91 ~]# ctr ns rm hsc
hsc
[root@elk91 ~]#
[root@elk91 ~]# ctr ns ls
NAME LABELS
moby
haoshuaicong
[root@elk91 ~]# 3. ctr 实现管理镜像
3.1 查看指定名称空间的镜像列表
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
[root@elk91 ~]# 3.2 拉取第三方镜像仓库
[root@elk91 ~]# ctr -n haoshuaicong image pull registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1: resolved |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:2c6e86e57dfd729d8240ceab7c18bd1e5dd006b079837116bc1c3e1de5e1971a: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 2.6 s total: 8.9 Mi (3.4 MiB/s)
unpacking linux/amd64 sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c...
done: 404.865087ms
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]# 3.3 给镜像打标签
[root@elk91 ~]# ctr -n haoshuaicong image tag registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 haoshuaicong:hsc
haoshuaicong:hsc
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
haoshuaicong:hsc application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]# 3.4 拉取 Harbor 自建的仓库镜像
[root@elk91 ~]# ctr -n haoshuaicong image pull harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15: resolved |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:fb18e9be5a61691dac57fcb404b58dff9eced05ebd6e101a4fbf6e300fa4c948: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:76e5593f66e22f787441854a93a68e4d2b9f6446de54f77983b159288f244e06: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 0.6 s total: 18.6 M (30.9 MiB/s)
unpacking linux/amd64 sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72...
done: 399.931153ms
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15 application/vnd.docker.distribution.manifest.v2+json sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72 21.2 MiB linux/amd64 -
haoshuaicong:hsc application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]# 3.5 删除镜像
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15 application/vnd.docker.distribution.manifest.v2+json sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72 21.2 MiB linux/amd64 -
haoshuaicong:hsc application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]#
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image rm haoshuaicong:hsc
haoshuaicong:hsc
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15 application/vnd.docker.distribution.manifest.v2+json sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72 21.2 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]# 3.6 拉取官方的镜像
注意: 他不认识docker默认不是docker拉取,需要指定 docker.io 拉取docker官网的镜像
[root@elk91 ~]# export http_proxy="http://10.0.0.1:7890"
[root@elk91 ~]# export https_proxy=http://10.0.0.1:7890
[root@elk91 ~]#
[root@elk91 ~]# env | grep -i http
https_proxy=http://10.0.0.1:7890
http_proxy=http://10.0.0.1:7890
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image pull docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1: resolved |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:bac97e2f09ed597756380324f551dc1d63d44bc3ce2fd8bebd98af413896f006: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 9.3 s total: 2.0 Mi (223.2 KiB/s)
unpacking linux/amd64 sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259...
done: 110.402829ms
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15 application/vnd.docker.distribution.manifest.v2+json sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72 21.2 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]# 4. 镜像导入,导出,推送镜像到 Harbor 仓库
4.1 导出镜像
# image 可以简写成 i
[root@elk91 ~]# ctr -n haoshuaicong i ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15 application/vnd.docker.distribution.manifest.v2+json sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72 21.2 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong image export haoshuaicong-stress.tar.gz docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1
[root@elk91 ~]#
[root@elk91 ~]# ll haoshuaicong-stress.tar.gz
-rw-r--r-- 1 root root 2856960 Mar 25 16:17 haoshuaicong-stress.tar.gz
[root@elk91 ~]#
[root@elk91 ~]# scp haoshuaicong-stress.tar.gz 10.0.0.93:~
haoshuaicong-stress.tar.gz 100% 2790KB 59.9MB/s 00:00 4.2 导入镜像
[root@elk93 ~]# ln -svf /var/run/docker/containerd/containerd.sock /run/containerd/
'/run/containerd/containerd.sock' -> '/var/run/docker/containerd/containerd.sock'
[root@elk93 ~]#
[root@elk93 ~]# ctr ns ls
NAME LABELS
moby
[root@elk93 ~]#
[root@elk93 ~]# ctr image import haoshuaicong-stress.tar.gz # 如果不指定名称空间,则默认导入到'default'名称空间。
unpacking docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 (sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259)...done
[root@elk93 ~]#
[root@elk93 ~]# ctr ns ls
NAME LABELS
default
moby
[root@elk93 ~]#
[root@elk93 ~]# ctr image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
[root@elk93 ~]#
[root@elk93 ~]#
[root@elk93 ~]# ctr -n moby image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
[root@elk93 ~]#
[root@elk93 ~]# ctr -n default image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 - 4.3 推送镜像到 http 仓库
[root@elk93 ~]# ctr image tag docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 10.0.0.91/haoshuaicong-containerd/stress:v0.1
10.0.0.91/haoshuaicong-containerd/stress:v0.1
[root@elk93 ~]#
[root@elk93 ~]# ctr -n default image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
10.0.0.91/haoshuaicong-containerd/stress:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
[root@elk93 ~]#
[root@elk93 ~]# ctr image push --plain-http -u admin:1 10.0.0.91/haoshuaicong-containerd/stress:v0.1
manifest-v0.1@sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:da6fdb7c9168278f1f455522fcd2f88b5ed2d240a89feca10e7eda3f8ffacd5e: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 0.2 s
total: 3.6 Ki (17.7 KiB/s)
# 推送镜像,http不加密
# 注意push 时 --plain-http 表示允许 http 协议推送
# -u 指定用户名密码 admin:1
ctr image tag xxx镜像 xxx自定义tag镜像
ctr image push --plain-http -u admin:1 xxx自定义tag镜像 4.4 推送镜像到 https 仓库
默认走的就是https协议
但是,证书是自己生成的,-k 忽略证书校验
[root@elk93 ~]# ctr image tag docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 harbor250.haoshuaicong.com/library/stress:v0.2
harbor250.haoshuaicong.com/library/stress:v0.2
[root@elk93 ~]#
[root@elk93 ~]# ctr -n default image ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
10.0.0.91/haoshuaicong-containerd/stress:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
harbor250.haoshuaicong.com/library/stress:v0.2 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
[root@elk93 ~]#
[root@elk93 ~]# ctr image push -u admin:1 -k harbor250.haoshuaicong.com/library/stress:v0.2
manifest-v0.1@sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:da6fdb7c9168278f1f455522fcd2f88b5ed2d240a89feca10e7eda3f8ffacd5e: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 0.3 s total: 3.6 Ki (11.9 KiB/s) 4.5 到相应的 Harbor 仓库查看镜像是否推送成功
可能会遇到的报错及解决方案
报错 Q1
[root@elk93 ~]# ctr image push 10.0.0.91/haoshuaicong-containerd/stress:v0.1
manifest-v0.1@sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259: waiting |--------------------------------------|
config-sha256:da6fdb7c9168278f1f455522fcd2f88b5ed2d240a89feca10e7eda3f8ffacd5e: waiting |--------------------------------------|
elapsed: 0.1 s total: 0.0 B (0.0 B/s)
ctr: failed to do request: Head "https://10.0.0.91/v2/haoshuaicong-containerd/stress/blobs/sha256:cdc010c9a8492436224fd138b6758bdbb4930f7fed029d4a992f61a84c058c38": dial tcp 10.0.0.91:443: connect: connection refused- 问题原因:默认走的是 https 协议,需要指定 http 协议。
- 解决方案:使用
--plain-http参数。
报错 Q2
[root@elk93 ~]# ctr image push --plain-http 10.0.0.91/haoshuaicong-containerd/stress:v0.1
manifest-v0.1@sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259: waiting |--------------------------------------|
config-sha256:da6fdb7c9168278f1f455522fcd2f88b5ed2d240a89feca10e7eda3f8ffacd5e: waiting |--------------------------------------|
elapsed: 0.1 s total: 0.0 B (0.0 B/s)
ctr: unexpected status: 401 Unauthorized- 问题原因:认证失败。
- 解决方案:指定正确的用户名和密码。
ctr 管理容器实战
1. 创建容器
[root@elk91 ~]# ctr -n haoshuaicong containers create registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 xiuxain
[root@elk91 ~]# 2. 查看容器列表
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
xiuxain registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers create registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 xixi
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers create registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 haha
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
haha registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
xiuxain registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
xixi registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]# 3. 删除容器
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
haha registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
xiuxain registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
xixi registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers rm xixi
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
haha registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
xiuxain registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers rm xixi
ERRO[0000] failed to delete container "xixi" error="container \"xixi\" in namespace \"haoshuaicong\": not found"
ctr: container "xixi" in namespace "haoshuaicong": not found
[root@elk91 ~]#
[root@elk91 ~]#
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers rm haha xiuxain
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
[root@elk91 ~]# 4. 查看容器的详细信息
[root@elk91 ~]# ctr -n haoshuaicong containers create registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 xiuxian
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
xiuxian registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers info xiuxian
{
"ID": "xiuxian",
"Labels": {
"com.docker.compose.project": "dockerfile",
"com.docker.compose.service": "apps_v1",
"com.docker.compose.version": "2.23.0",
"io.containerd.image.config.stop-signal": "SIGQUIT",
"maintainer": "NGINX Docker Maintainers \u003cdocker-maint@nginx.com\u003e"
},
"Image": "registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1",
...
}ctr 管理 task 任务及 docker 底层调用的是 task
1. 基于容器启动任务
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
xiuxian registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task start -d xiuxian
/docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
/docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
/docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
xiuxian 657511 RUNNING
[root@elk91 ~]# 2. 连接指定容器
[root@elk91 ~]#
/ #
/ # ps -ef
PID USER TIME COMMAND
1 root 0:00 nginx: master process nginx -g daemon off;
24 nginx 0:00 nginx: worker process
25 nginx 0:00 nginx: worker process
39 root 0:00 sh
45 root 0:00 ps -ef
/ #
/ # ifconfig -a # Containerd创建的容器默认是不会分配网络的!
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
/ #
/ # 如果想要让 Containerd 拥有网络,可以单独配置 CNI (Container Network Interface) 网络插件。
3. 暂停任务
[root@elk91 ~]# ctr -n haoshuaicong task pause xiuxian
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
xiuxian 657511 PAUSED
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task exec -t --exec-id $RANDOM xiuxian sh
ctr: cannot exec in a paused state: unknown
[root@elk91 ~]# 4. 恢复暂停任务
[root@elk91 ~]# ctr -n haoshuaicong task resume xiuxian
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
xiuxian 657511 RUNNING
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task exec -t --exec-id $RANDOM xiuxian sh
/ # curl 127.0.0.1
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8"/>
<title>haoshuaicong apps v1</title>
<style>
div img {
width: 900px;
height: 600px;
margin: 0;
}
</style>
</head>
<body>
<h1 style="color: green">凡人修仙传 v1 </h1>
<div>
<img src="1.jpg">
<div>
</body>
</html>
/ #
[root@elk91 ~]# 5. 查看容器的 metric 指标
[root@elk91 ~]# ctr -n haoshuaicong task metrics xiuxian
ID TIMESTAMP
xiuxian 2025-03-25 09:16:02.511217378 +0000 UTC
METRIC VALUE
pids.current 3
pids.limit 18446744073709551615
cpu.usage_usec 48273
cpu.user_usec 4022
cpu.system_usec 44250
cpu.nr_periods 0
cpu.nr_throttled 0
cpu.throttled_usec 0
memory.usage 3133440
memory.usage_limit 18446744073709551615
memory.swap_usage 0
memory.swap_limit 18446744073709551615
[root@elk91 ~]# 6. 停止任务
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
xiuxian 657511 RUNNING
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task kill xiuxian
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
xiuxian 657511 STOPPED
[root@elk91 ~]# 7. 移除任务
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
xiuxian 657511 STOPPED
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task rm xiuxian
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong containers ls
CONTAINER IMAGE RUNTIME
xiuxian registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]# 彩蛋:docker 容器底层调用的就是 Containerd 的 task
[root@elk91 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
2f312a5a92f4 registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v2 "/docker-entrypoint.…" 2 hours ago Up 2 hours 0.0.0.0:83->80/tcp, :::83->80/tcp hopeful_chatelet
81fa6ecb48d8 registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 "/docker-entrypoint.…" 2 hours ago Up 2 hours 0.0.0.0:82->80/tcp, :::82->80/tcp youthful_heyrovsky
fac34f9f8df0 10.0.0.91/haoshuaicong-dockerfile/demo:v0.1 "tail -f /etc/hosts" 8 hours ago Up 8 hours haoshuaicong-xixi-1
07bf3ec8383b goharbor/harbor-jobservice:v2.12.2 "/harbor/entrypoint.…" 8 hours ago Up 8 hours (healthy) harbor-jobservice
d981823a63c7 goharbor/nginx-photon:v2.12.2 "nginx -g 'daemon of…" 8 hours ago Up 8 hours (healthy) 0.0.0.0:80->8080/tcp, :::80->8080/tcp nginx
6cd797e0b9ae goharbor/harbor-core:v2.12.2 "/harbor/entrypoint.…" 8 hours ago Up 8 hours (healthy) harbor-core
2bb763a9a475 goharbor/registry-photon:v2.12.2 "/home/harbor/entryp…" 8 hours ago Up 8 hours (healthy) registry
e77f92bf46e2 goharbor/redis-photon:v2.12.2 "redis-server /etc/r…" 8 hours ago Up 8 hours (healthy) redis
66cd3c358dad goharbor/harbor-portal:v2.12.2 "nginx -g 'daemon of…" 8 hours ago Up 8 hours (healthy) harbor-portal
040d73767541 goharbor/harbor-db:v2.12.2 "/docker-entrypoint.…" 8 hours ago Up 8 hours (healthy) harbor-db
5423993a92ef goharbor/harbor-registryctl:v2.12.2 "/home/harbor/start.…" 8 hours ago Up 8 hours (healthy) registryctl
ef54d6861ddc goharbor/harbor-log:v2.12.2 "/bin/sh -c /usr/loc…" 8 hours ago Up 8 hours (healthy) 127.0.0.1:1514->10514/tcp harbor-log
[root@elk91 ~]#
[root@elk91 ~]# ctr -n moby task ls
TASK PID STATUS
fac34f9f8df0ae31af81084e7d6a36916c726be2ba18dc247a144526c4bee4a6 484942 RUNNING
ef54d6861ddc11e88872e9c472d99a99ee0bae68a2da74fe5c89e6b22a9a470b 483300 RUNNING
66cd3c358dad4b3b554b8a6c92d1f93200bc0ffcfa8605daf91c6d0290d05df8 483452 RUNNING
e77f92bf46e2cc1c2c32a8e63f401cd70df69cebd96913f912a60daec8f90bef 483504 RUNNING
6cd797e0b9ae82b4a9bbcf7ee9d35e72c8b0a0ba7e926d0a11b5f571b42aba12 483803 RUNNING
d981823a63c7e3d0fefaca312c1ae08dfd66167a3cc813164223715019de8cb0 483964 RUNNING
81fa6ecb48d8376a83bfb46e73df4b98e0478f7a3c124df6a653b6a93481969e 608556 RUNNING
2f312a5a92f4ed6c022ef996cf4d80116cdd961681efa13101cfa3a52b65976d 608886 RUNNING
040d7376754192a57e3a918b600c433a58dd9370ce9136d861f3e1b0647faf05 483385 RUNNING
5423993a92ef84f81be453516587caad73a2c4c87bd18d9518f23f1ee1cb21c1 483551 RUNNING
2bb763a9a4753fb30300e022a3d85084cda15409ec1e8ff30b9b52117d8c41f5 483586 RUNNING
07bf3ec8383bcdc82a65a44f8acb8b40b2fe5cc4cb1a9928cc26c43147cd3f4d 483939 RUNNING
[root@elk91 ~]#
[root@elk91 ~]#
[root@elk91 ~]# docker inspect -f "{{ .State.Pid}}" harbor-log
483300
[root@elk91 ~]# Containerd 存储卷案例
1. 创建容器并运行任务
[root@elk91 ~]# ctr -n haoshuaicong i ls
REF TYPE DIGEST SIZE PLATFORMS LABELS
docker.io/haoshuaicong2020/haoshuaicong-linux-tools:v0.1 application/vnd.docker.distribution.manifest.v2+json sha256:eac6c50d80c7452db54871790fb26a6ca4d63dd3d4c98499293b3bab90832259 2.7 MiB linux/amd64 -
harbor.haoshuaicong.com/haoshuaicong-linux/haoshuaicong-hsc:v2.15 application/vnd.docker.distribution.manifest.v2+json sha256:3e426de7fe466de0c975c279d3ac4e0bf07b869d4fe7b5cc43c7107bba75de72 21.2 MiB linux/amd64 -
registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 application/vnd.docker.distribution.manifest.v2+json sha256:3bee216f250cfd2dbda1744d6849e27118845b8f4d55dda3ca3c6c1227cc2e5c 9.6 MiB linux/amd64 -
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong c ls
CONTAINER IMAGE RUNTIME
xiuxian registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong run -d registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 xianni
/docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
/docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
/docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong c ls
CONTAINER IMAGE RUNTIME
xianni registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
xiuxian registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 io.containerd.runc.v2
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong t ls
TASK PID STATUS
xianni 665726 RUNNING
[root@elk91 ~]# 2. Container 支持存储卷只读的方式
[root@elk91 ~]# ctr -n haoshuaicong run -d --mount type=bind,src=/haoshuaicong,dst=/hsc,options=rbind:ro registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 doupocangqiong
/docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
/docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
/docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
doupocangqiong 668824 RUNNING
xianni 665726 RUNNING
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task exec -t --exec-id $RANDOM doupocangqiong sh
/ #
/ # ls -l /hsc/
total 8
drwxr-xr-x 3 root root 4096 Mar 16 08:52 data
drwxr-xr-x 3 root root 4096 Mar 24 07:55 softwares
/ #
/ # ls -l /hsc/softwares/
total 4
drwxrwxr-x 2 1000 1000 4096 Mar 24 07:55 docker
/ #
/ # ls -l /hsc/softwares/docker/
total 255180
-rwxr-xr-x 1 1000 1000 39451064 Apr 4 2023 containerd
-rwxr-xr-x 1 1000 1000 7548928 Apr 4 2023 containerd-shim
-rwxr-xr-x 1 1000 1000 9760768 Apr 4 2023 containerd-shim-runc-v2
-rwxr-xr-x 1 1000 1000 21090304 Apr 4 2023 ctr
-rwxr-xr-x 1 1000 1000 47955672 Apr 4 2023 docker
-rwxr-xr-x 1 root root 59628532 Mar 24 07:55 docker-compose
-rwxr-xr-x 1 1000 1000 765808 Apr 4 2023 docker-init
-rwxr-xr-x 1 1000 1000 2628514 Apr 4 2023 docker-proxy
-rwxr-xr-x 1 1000 1000 58246432 Apr 4 2023 dockerd
-rwxr-xr-x 1 1000 1000 14214624 Apr 4 2023 runc
/ #
/ #
/ # cp /etc/os-release /hsc/softwares/docker/
cp: can't create '/hsc/softwares/docker/os-release': Read-only file system
/ #
/ # 3. Container 支持存储卷读写的方式
[root@elk91 ~]# ctr -n haoshuaicong run -d --mount type=bind,src=/haoshuaicong,dst=/hsc,options=rbind:rw registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 zhetian
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong t ls
TASK PID STATUS
xianni 665726 RUNNING
doupocangqiong 668824 RUNNING
zhetian 670658 RUNNING
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task exec -t --exec-id $RANDOM zhetian sh
/ # ls /hsc/
data softwares
/ #
/ # cp /etc/os-release /hsc/
/ #
/ # ls /hsc/
data os-release softwares
/ #
/ #
[root@elk91 ~]#
[root@elk91 ~]# ls /haoshuaicong/
data os-release softwares
[root@elk91 ~]# 3. 快照功能
略
4. Containerd 可以和宿主机共享网络(相当于 docker run --network host ...)
[root@elk91 ~]# ctr -n haoshuaicong run -d --net-host registry.cn-hangzhou.aliyuncs.com/haoshuaicong-k8s/apps:v1 xixi tail -f /etc/hosts
127.0.1.1 haoshuaicong
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.0.0.250 harbor250.haoshuaicong.com
10.0.0.93 harbor.haoshuaicong.com
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task ls
TASK PID STATUS
doupocangqiong 668824 RUNNING
zhetian 670658 RUNNING
xixi 687593 RUNNING
xianni 665726 RUNNING
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task exec --exec-id $RANDOM -t xixi
ctr: OCI runtime exec failed: exec failed: args must not be empty: unknown
[root@elk91 ~]#
[root@elk91 ~]# ctr -n haoshuaicong task exec --exec-id $RANDOM -t xixi sh
/ #
/ # ifconfig
br-e3936bac3b41 Link encap:Ethernet HWaddr 02:42:DE:B6:B5:BB
inet addr:172.19.0.1 Bcast:172.19.255.255 Mask:255.255.0.0
inet6 addr: fe80::42:deff:feb6:b5bb/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:29 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:4108 (4.0 KiB)
docker0 Link encap:Ethernet HWaddr B2:B3:56:B9:11:98
inet addr:172.17.0.1 Bcast:172.17.255.255 Mask:255.255.0.0
inet6 addr: fe80::b0b3:56ff:feb9:1198/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:55 errors:0 dropped:0 overruns:0 frame:0
TX packets:84 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:456278 (445.5 KiB) TX bytes:10193 (9.9 KiB)
eth0 Link encap:Ethernet HWaddr 00:0C:29:AD:27:87
inet addr:10.0.0.91 Bcast:10.0.0.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fead:2787/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:102491982 errors:0 dropped:0 overruns:0 frame:0
TX packets:95390025 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:24588241331 (22.8 GiB) TX bytes:25956184654 (24.1 GiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:69387498 errors:0 dropped:0 overruns:0 frame:0
TX packets:69387498 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:8448729181 (7.8 GiB) TX bytes:8448729181 (7.8 GiB)
veth5a7ece7 Link encap:Ethernet HWaddr 32:4F:78:2D:77:66
inet6 addr: fe80::304f:78ff:fe2d:7766/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:29 errors:0 dropped:0 overruns:0 frame:0
TX packets:63 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:236791 (231.2 KiB) TX bytes:7343 (7.1 KiB)面试题:docker 和 Containerd 的区别?
相同点
- 都是 Docker Inc 公司研发,Containerd 在 2017 年被捐献给了 CNCF 组织。相关链接:https://landscape.cncf.io/
- 都支持容器管理、镜像管理和存储卷功能管理。
- 都支持镜像的推送和拉取。
不同点
- Containerd 的容器启动时必须本地有镜像,不会自动拉取。
- Containerd 存在名称空间的概念。
- Containerd 将容器和任务分开管理。
- Containerd 支持快照功能。
- Containerd 没有自定义的网络,需要单独安装 CNI 插件。
- Containerd 不支持镜像的编译。
生产环境该如何选择容器管理工具呢?
- 如果没有特殊需求,建议使用 Docker,因为 Docker 底层调用了 Containerd 的 task,便于管理,而且支持丰富的网络功能。
- 但是对于 K8S 1.24+ 版本而言,默认就是用 Containerd 作为容器运行时, K8S 使用。
今日命令总结
# docker查看容器的进程
docker top haha
# 编译docker-compose,需要在相应目录
docker-compose build
# 推送编译好的docker-compose,前提是提前打好了推动服务器地址标签tag
docker-compose push
# docker-compose 删除,启动,查看。启动需要再相应目录,有docker-compose.yml文件
docker-compose down -t 0
docker-compose up -d
docker-compose ps
空间ns
镜像image
容器containers
# containerd 管理名称空间
# 查看名称空间
crt ns ls
# 创建名称空间
ctr ns create haoshuaicong
# 删除名称空间
ctr ns create haoshuaicong
# containerd 管理镜像
# 查看指定名称空间的镜像列表
ctr -n haoshuaicong image ls
# 拉取镜像到haoshuaicong名称空间
ctr -n haoshuaicong image pull xxx镜像
# 给镜像打tag标签
ctr -n haoshuaicong image tag xxx xxx
# 删除镜像(注意是haoshuaicong名称空间的镜像)
ctr -n haoshuaicong image rm xxx镜像
# 导入镜像,import 。如果不 -n 指定名称空间,则默认导入到'default'名称空间。
crt -n haoshuaicong image import xxxx.tar.gz
# 导出镜像,export
crt -n haoshuaicong image export xxx.tar.gz xxx镜像
# 推送镜像
# 注意push 时 --plain-http 表示允许 http 协议推送
# 那如果推送的是https 报错证书不合法,使用-k 忽略证书校验
# -u 指定用户名密码 admin:1
ctr image tag xxx镜像 xxx自定义tag镜像
ctr image push --plain-http -u admin:1 xxx自定义tag镜像
ctr image push --plain-http -u -k admin:1 xxx自定义tag镜像
# 管理容器 ctr containers 简写 ctr c
# 查看容器
ctr -n haoshuaicong containers ls
# 创建容器,跟docker创建容器一样,创建后creatd状态,不启动。
ctr -n haoshuaicong containers create xxx镜像 xixi
# 删除容器
ctr -n haoshuaicong containers rm xixi
# 查看容器详细信息
ctr -n haoshuaicong containers info xixi
# 任务管理taks
# 查看
ctr -n haoshuaicong task ls
# 启动容器,任务
ctr -n haoshuaicong task start -d xixi
# 连接指定容器,-t分配一个终端
# 另外需要指定一个随机 id 数字使用 --exec-id ,这里$RANDOM表示随机数
ctr -n haoshuaicong task exec -t --exec-id 123 xixi sh
ctr -n haoshuaicong task exec -t --exec-id $RANDOM xixi sh
# ctr 启动的容器没有网课,只要回环地址,如果想要让 Containerd 拥有网络,可以单独配置 CNI (Container Network Interface) 网络插件。
# 暂停pause
ctr -n haoshuaicong task pause xixi
# 恢复
ctr -n haoshuaicong task resume xixi
# 停止任务
ctr -n haoshuaicong task kill xixi
# 删除任务,但是容器还在
ctr -n haoshuaicong task rm xixi
# 查看容器的 metric 指标
ctr -n haoshuaicong task metrics xiuxian
# 创建容器并运行
ctr -n haoshuaicong run -d xxx镜像 xixi
# 存储卷只读的方式,挂载类型bind,宿主机路径src。容器挂载路径dst。options=rbind:ro 只读
ctr -n haoshuaicong run -d --mount type=bind,src=/haoshuaicong,dst=/hsc,options=rbind:ro xxx镜像 xixi
# 存储卷,读写方式
ctr -n haoshuaicong run -d --mount type=bind,src=/haoshuaicong,dst=/hsc,options=rbind:rw xxx镜像 haha
# 使用宿主机网络 --net-host
ctr -n haoshuaicong run -d --net-host xxx镜像 xixi